TIME – Attacks on the TLS Record Protocol
21.5.5 TIME
Less than a year after CRIME was published, security researchers Tal Be’ery and Amichai Shulman presented a new attack they called Timing Info-leak Made Easy (TIME) [17]. Conceptually, TIME can be seen as an improvement of the CRIME attack because it eliminates two constraints from the attacker model, and therefore requires a less powerful attacker.
CRIME targets secret values contained in a compressed HTTP request. However, soon after CRIME was published, TLS stopped supporting HTTP request compression, thereby making CRIME less dangerous in practice.
TIME, on the other hand, targets HTTP responses. Because a typical HTTP response is much larger than the HTTP request, compressing the responses is a popular technique used by web servers to speed up data transmission. As a result, the compression feature exploited by TIME – and, therefore, TIME’s attacker model – has more practical relevance.
CRIME’s second constraint relates to network access. To mount the CRIME attack, Eve must have access to the encrypted network traffic. In other words, she not only must trick Bob into executing malicious JavaScript code, but also needs to be in a man-in-the-middle position where she can intercept Bob’s encrypted traffic.
TIME, on the other hand, uses differential timing analysis to infer the size of the encrypted data. More precisely, Eve guesses the secret value she wants to extract and measures differences in the transmission time of Alice’s encrypted HTTP response to Bob. If a sufficiently large part of Eve’s guess is correct, the payload of the HTTP response will be smaller and, therefore, the transmission time will be shorter.
The main advantage of exploiting the timing side channel rather than inspecting the encrypted traffic is that the time measurement can be done in the JavaScript code. In other words, Eve does not need man-in-the-middle access to the network traffic transmitted between Alice and Bob. This makes a huge difference. Think about our discussion of local versus remote attacks in chapter 19, Attacks on Cryptography. In practice, the requirement to observe Bob’s network traffic most likely means that Eve must get access to Bob’s wireless local area network. Eve must be co-located with Bob while she performs the attack. On the face of it, CRIME looks like a remote attack because it targets network traffic. The need for Eve to access Bob’s traffic, however, makes CRIME a local attack.
On the other hand, basically any malicious website that Bob visits can have JavaScript code embedded in it that launches the TIME attack, so TIME is a remote attack.
But how does Eve manage to measure small timing differences over the internet? It turns out that she can do this using the so-called congestion window (see Figure 21.3), a feature of the TCP protocol that underlies TLS [150]. To avoid the link between the sender and the receiver becoming overloaded with too much traffic, TCP’s congestion window limits the number of bytes that can be transmitted at once.
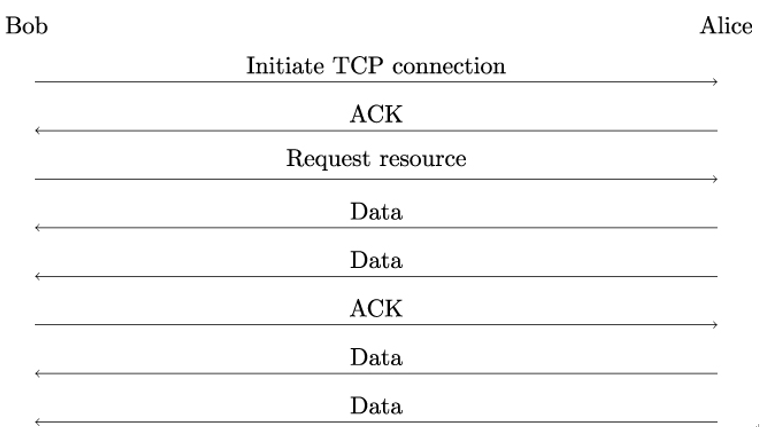
Figure 21.3: Working principle of the TCP congestion window
If the payload to be sent is larger than the congestion window, the sender transmits the first part of the payload that fits into the congestion window, waits for the TCP acknowledgment message from the receiver, and transmits the remaining data. This, in turn, introduces one Round-Trip Time (RTT).Figure 21.3 shows an example where the congestion window has the size of two TCP segments. After Bob requests a resource, for example, a web page, Alice sends two segments of payload data – the size of the congestion window – and suspends the transmission waiting for Bob to acknowledge he received that data.
By correctly guessing part of the secret value, Eve can make the compressed HTTP response fit exactly into a single congestion window. As a result, a change of one byte in the payload will reduce the response time by one RTT. As an example, an RTT for data transmission between London and New York is approximately 90 ms [150] and therefore can be measured in JavaScript.
However, Eve must be able to inject her guesses into the page (served by Alice) that contains the secret Eve wants to extract. This means that the web application Eve is targeting must mirror some data transmitted in the HTTP request to this application in its HTTP response.
