Raccoon – Attacks on TLS Implementations
22.9.2 Raccoon
The Raccoon attack [118] provides an example of a timing attack against the TLS handshake. It allows attackers under certain conditions to get hold of the PreMasterSecret established in course of the TLS handshake. However, the authors of [118] themselves say this:
The vulnerability is really hard to exploit and relies on very precise timing measurements and on a specific server configuration to be exploitable.
The attack
Raccoon exploits the fact that according to the specification of TLS 1.2 (and all previous versions), all leading zero bytes in PreMasterSecret shall be deleted before the PMS is used in further computations. As the resulting PMS serves as input into the key derivation function KDF , which is in turn based on hash functions with different timing profiles, precise timing measurements may enable an attacker to find out whether the PMS starts with zero or not.
For example, if Diffie-Hellman is used to establish the PMS, Mallory could eavesdrop the values gα mod p sent by the client (where α is the client’s private key) in a ClientKeyExchange message, resend it to the server, and determine via precise time measurements whether the resulting PMS starts with zero or not.
In order to go beyond the leading byte of the PMS, Mallory constructs a series of related values gμi ⋅ gα mod p and sends them to the server. These lead to PreMasterSecrets
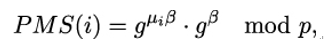
where β is the private key of the server. Note that this will only work if the server either uses static Diffie-Hellman or reuses ephemeral Diffie-Hellman keys for multiple connections.
Based on the server timing behavior, the attacker can find out which values will lead to PreMasterSecrets, starting with zero. This enables the attacker to construct a set of equations to compute the original PMS established between the client and the server.
Countermeasures in TLS 1.3
TLS 1.3 does not support static Diffie-Hellman-based key establishment. Apart from key establishment based on pre-shared keys (PSKs), only ephemeral Diffie-Hellman (DHE) or ephemeral elliptic-curve-based Diffie-Hellman (ECDHE) are available.
Their efficiency and the lack of detection makes side channel attacks a serious threat for any security system. Therefore, special design guidelines and dedicated countermeasures must be implemented to defend cryptographic circuits, in particular block ciphers, against this type of attack.
22.10 Summary
This chapter completes Part IV Bleeding Hearts and Biting Poodles, which was concerned with attacks on previous version of TLS. The attacks we covered in this chapter exploit implementation bugs rather than protocol weaknesses or vulnerabilities in underlying cryptographic mechanisms.
The SMACK and FREAK attacks are practical examples of how easily mistakes happen when you have to implement complex cryptographic protocols and algorithms. Indeed, to put it in the words of Bruce Schneier, complexity is the enemy of security. Remember: we had an initial discussion on this topic in the very first chapter of this book.
