BEAST – Attacks on the TLS Record Protocol
21.3 BEAST
Browser Exploit Against SSL/TLS (BEAST) [55] is an attack on the CBC-based encryption of the record layer in SSL 3.0 and TLS 1.0. It is not a padding oracle but uses the predictability of the IV (as mentioned previously, the IV is the last cipher block of the previous TLS record in these versions) instead of attacking one byte of the first cipher block in CBC mode. Using the bytewise privilege technique described earlier, Mallory can move interesting bytes within this cipher block and step-by-step decrypt the complete first cipher block. Still, because the attack is restricted to the first cipher block after the IV, the impact of BEAST was rather limited because the contents of the first plaintext block are usually known. However, BEAST pointed to the fact that there is a serious problem with CBC mode within the TLS record layer.
The attacker model is basically the same as for POODLE, that is, Mallory is a man-in-the-middle who is able to eavesdrop on and manipulate messages sent to the server, along with the ability to make the client send HTTPS requests crafted by him.
21.3.1 The attack
Let’s assume Mallory is interested in some unknown plaintext block m1, which must be the first plaintext block. The CBC mode encrypts m1 to
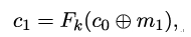
where Fk is the block cipher and c0 = IV . Mallory observes c1. Because he also knows c0, he can craft a new request to be sent by the client with the second plaintext block
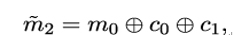
where m0 is some plaintext chosen by Mallory. This gets encrypted to
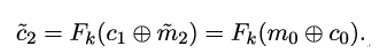
Mallory now observes c2 and uses an important fact to distinguish between m0 and m1: if m0 is equal to m1, then c1 = c2.
This means IND-CPA (see Section 15.1.1 in Chapter 15, Authenticated Encryption) is broken if the CBC mode is used with a predictable IV. The next step for Mallory is to make sure that the unknown plaintext m1 and m0 differ only by a single byte b, which is easy because most of the information in the first plaintext block (HTTP method, path, etc.) is known. As there are only 255 possibilities for b, it can be computed by Mallory by crafting at most 255 requests with the same m1 and different m0.
21.3.2 Countermeasures
Later versions of TLS, starting with version 1.1, use pseudorandomly generated IVs so that Mallory does not know the IV in advance. Still, because of the downgrade dance, patches were needed for TLS 1.0 and SSL 3.0. These patches make sure that the first plaintext block is always a meaningless dummy block that does not contain any sensitive data, such as authentication cookies.
